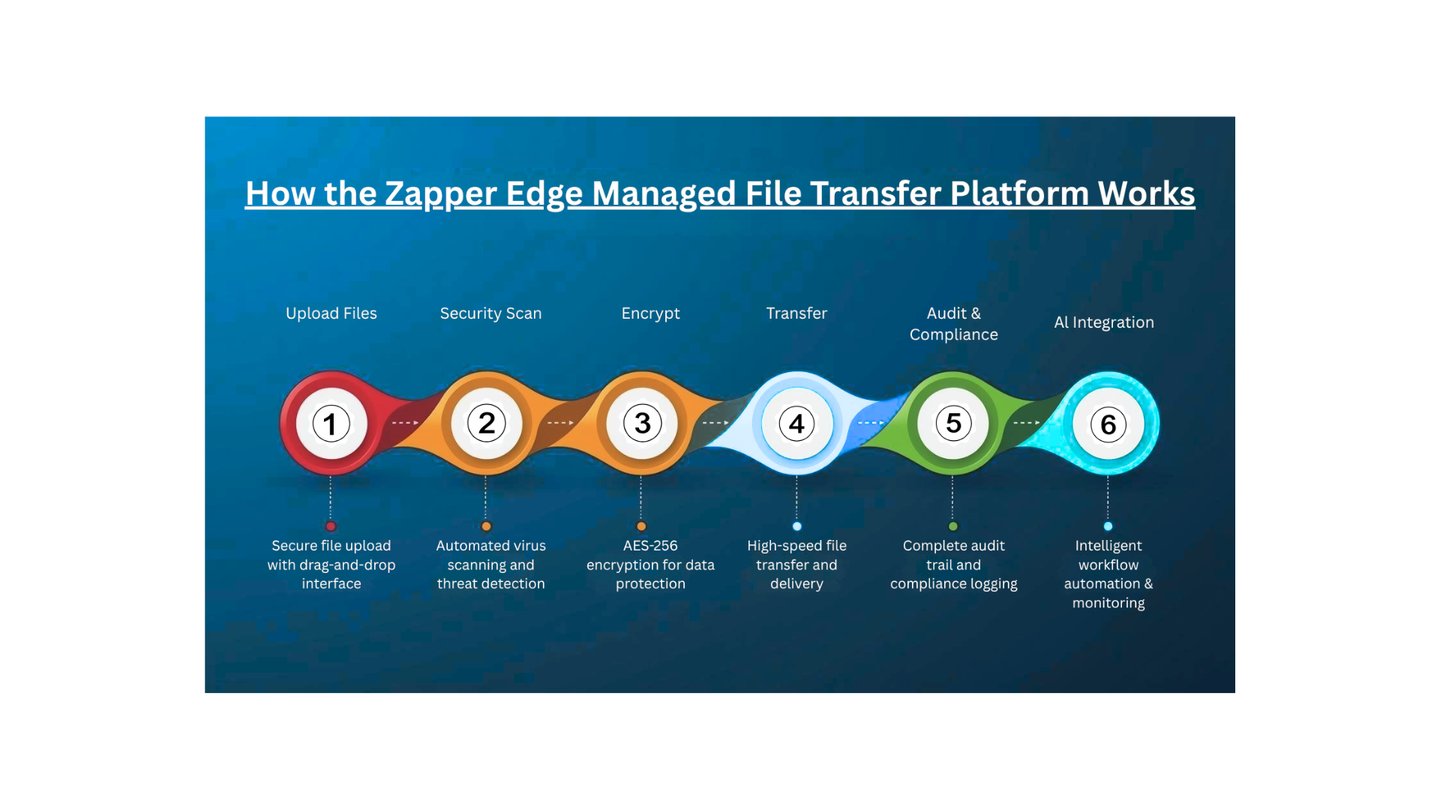
How Zapper Edge Managed File Transfer Platform Works






Chunked, Resumable Transfer Engine
Data Residency
Storage & Delivery
Observability & Control Plane
Secure Ingestion & Virus Scanning
All file uploads are automatically virus-scanned and validated before processing. Our multi-layered security approach includes real-time malware detection, content filtering, and file integrity verification to ensure only clean, safe files enter your system.
Real-time Scanning
Instant malware and virus detection
File type and integrity verification
Advanced threat detection feeds
Content Validation
Threat Intelligence
End-to-End Encryption
All files are encrypted in transit and at rest using AES-256 encryption with TLS protocols. Our zero-trust security model ensures your data remains protected throughout its entire lifecycle, from upload to delivery.
Automated Transfers & Workflows
Schedule and trigger file transfers via API with automated notifications and workflow orchestration. Our platform enables seamless integration with your existing systems through comprehensive APIs and webhook support.
Why This Design Matters?
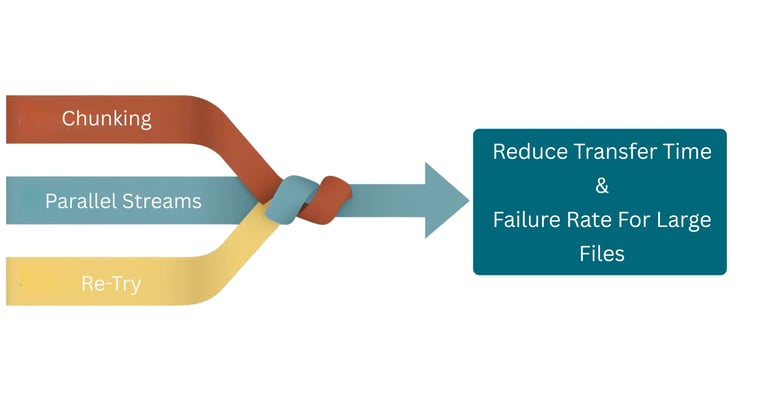
By leveraging chunking, parallel streams, and intelligent retry mechanisms, files are transmitted in smaller segments at a great speed and reliability. The architecture minimizes the impact of network fluctuations, ensuring a continuous and uninterrupted data flow. As a result, organizations experience significantly reduced transfer times and lower failure rates, enabling seamless and scalable file delivery.
Operational Considerations
Supported Client Methods
REST API
SFTP Bridge
Browser/CLI Client
Integration Hooks
API Calls
Failover Behavior
Automatic Resume
Retry Logic
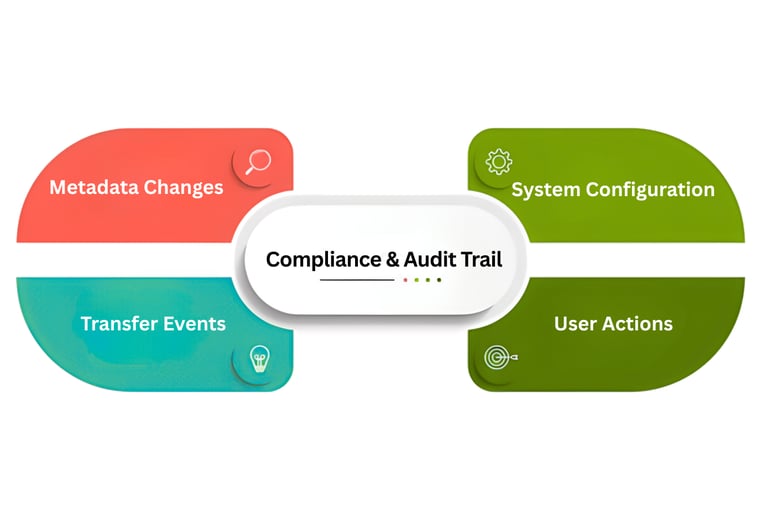
Compliance & Audit Trail
Transfer events, user actions, metadata changes and system configuration are recorded in tamper-resistant logs with built-in retention and export. These logs can be provided as part of compliance evidence.
ZapperEdge is engineered to operate on Azure's compliant substrate — helping customers meet GDPR, HIPAA and SOC-2 requirements (implementation and attestation depend on plan and deployment).
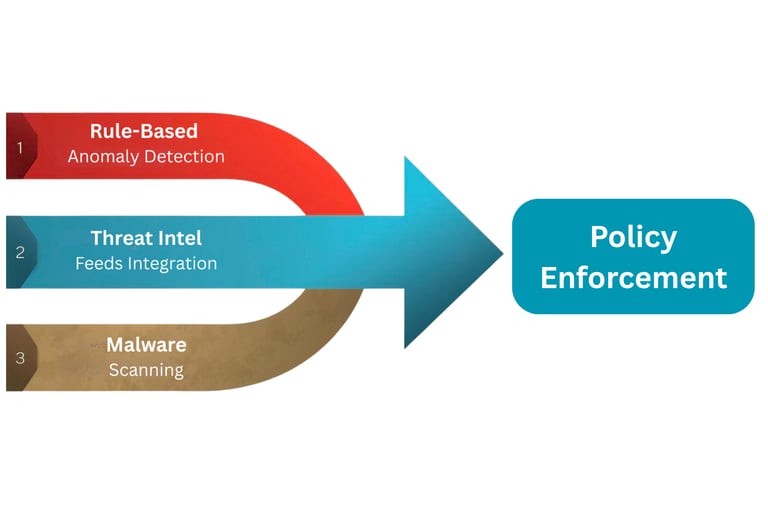
Threat Detection & Data Loss Prevention
At the core of a strong security framework is a layered defense strategy. Our approach begins with Rule-Based Anomaly Detection, which continuously monitors activity to identify unusual patterns and suspicious behavior. By combining these layers into a single, streamlined enforcement engine, we deliver strong, consistent, and proactive protection—keeping your data secure and resilient against evolving threats.
Connect
Secure file transfers made simple.
Support@zapperedge.com
© 2025. All rights reserved.
