Storage Creation Permission Error
When creating a new storage account through the Zapper Edge portal you may see a “Creation Failed” alert. The error usually looks like this:
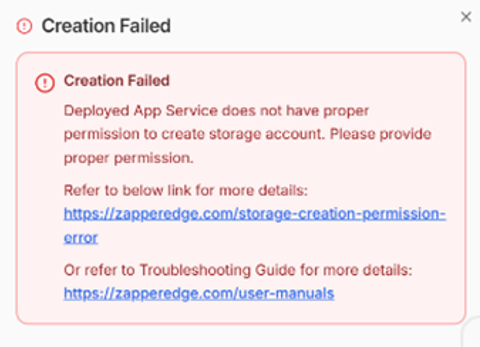
The message indicates that the deployed App Service does not have permission to create the storage account. The following guide explains the cause of the error and provides step‑by‑step instructions to resolve it.
Error Summary
The portal displays an error stating that the client does not have authorization to perform Microsoft.Resources/subscriptions/resourcegroups/read over the specified scope. This means the managed identity used by the App Service is missing the necessary roles to create storage resources. To fix the problem, you need to grant the App Service appropriate role‑based access control (RBAC) permissions at the subscription level.
Root Cause
This issue typically arises because:
The managed identity associated with the App Service does not have the Contributor, Storage Blob Data Contributor, and Defender for Storage Scanner Operator roles on the subscription.
Permissions were added after the app was deployed but the app’s credentials were not refreshed.
The scope of the role assignment (subscription or resource group) was misconfigured or inaccessible.
Step-by-Step Resolution
Follow these steps in the Azure portal to assign the required roles to your App Service’s managed identity. Use the Zapper Edge Subscription → Access control (IAM) page under the subscription where you want to create the storage account:
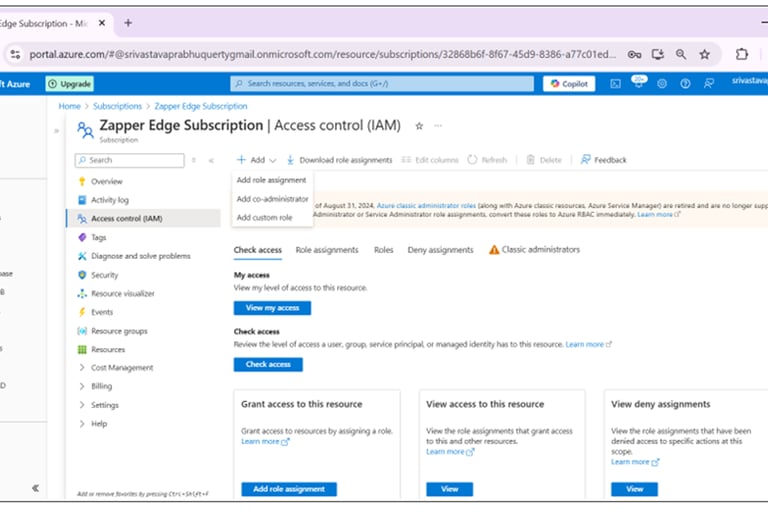
Creation Failed error screenshot
Access control (IAM) page
In the Azure portal, go to Subscriptions → Access control (IAM) for your subscription.
Select Add role assignment.
In the Role tab, search for and select Contributor. This role grants full access to manage all Azure resources, including the ability to assign roles. Click Next.
In the Members tab, choose Managed identity and click Select members. Search for and select the managed identity associated with your App Service (for example, the container app or function app). Click Select then Next.
Review the assignment and click Review + assign to grant the role.
The following screens illustrate the steps for selecting the Contributor role and managed identity:
Step 1 — Grant the “Contributor” Role
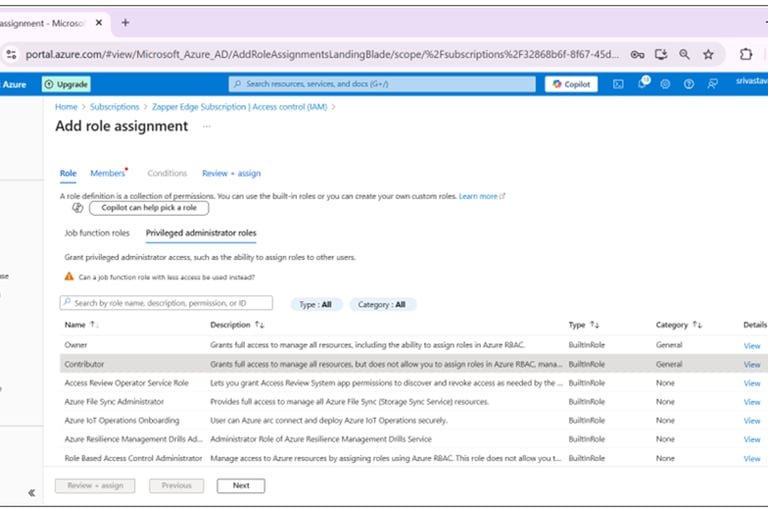
Selecting the Contributor role
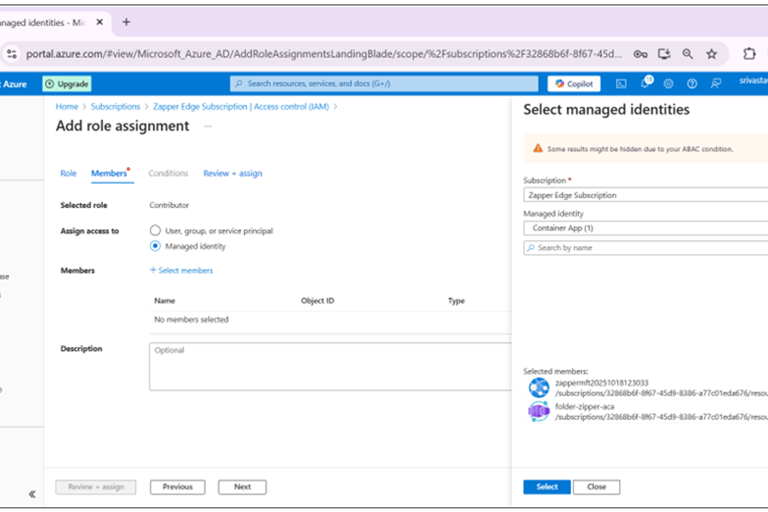
Assigning the Contributor role to the managed identity
Step 2 — Grant the “Storage Blob Data Contributor” Role
Still on the Access control (IAM) page, select Add role assignment again.
Search for Storage Blob Data Contributor. This role allows read, write and delete access to Azure Storage blob containers and data.
Select Storage Blob Data Contributor and click Next.
Under Members, choose Managed identity and select the same managed identity used in Step 1. Click Select then Next.
Review and assign the role.
These screens show how to search for the storage blob role and assign it to the managed identity:
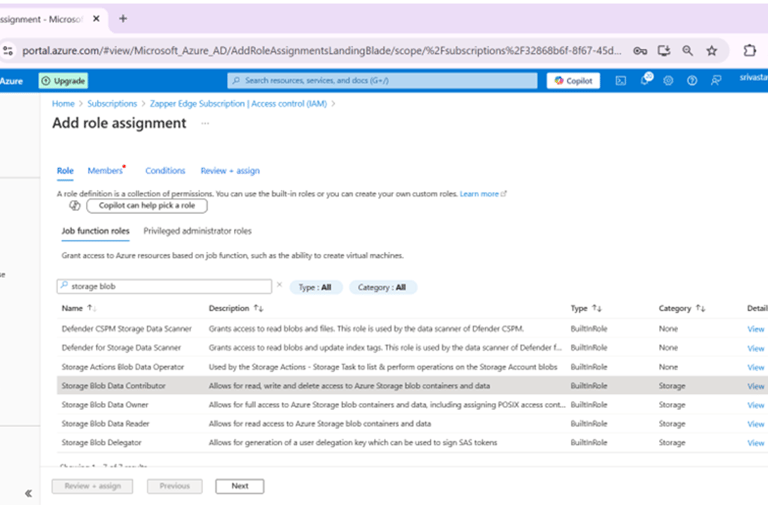
Searching for the Storage Blob Data Contributor role
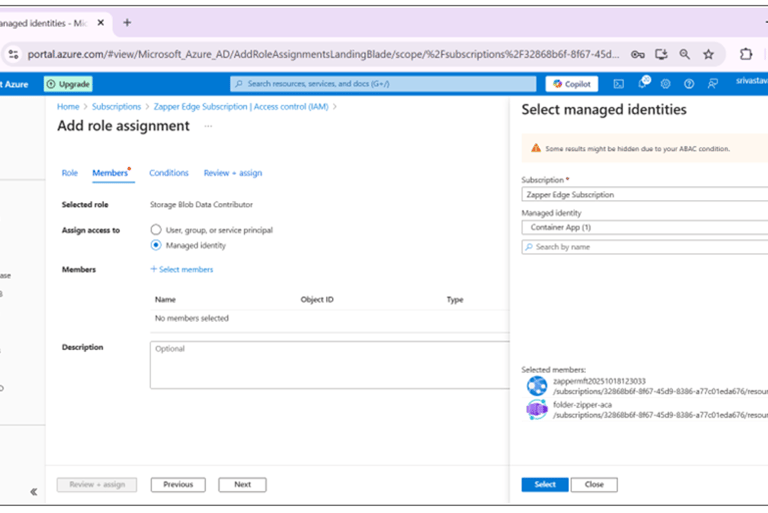
Assigning the Storage Blob Data Contributor role to the managed identity
Step 3 — Enable the “Defender for Storage Scanner Operator” Role
Once again select Add role assignment.
Search for Defender for Storage Scanner Operator. This built‑in role lets your app enable and configure Azure Defender for Storage’s malware and sensitive data scanning on storage accounts.
Select the Defender for Storage Scanner Operator role and click Next.
Under Members, pick Managed identity and select the same managed identity. Click Select then Next.
Review and assign the role.
The following screenshots illustrate selecting the Defender role and completing the assignment:
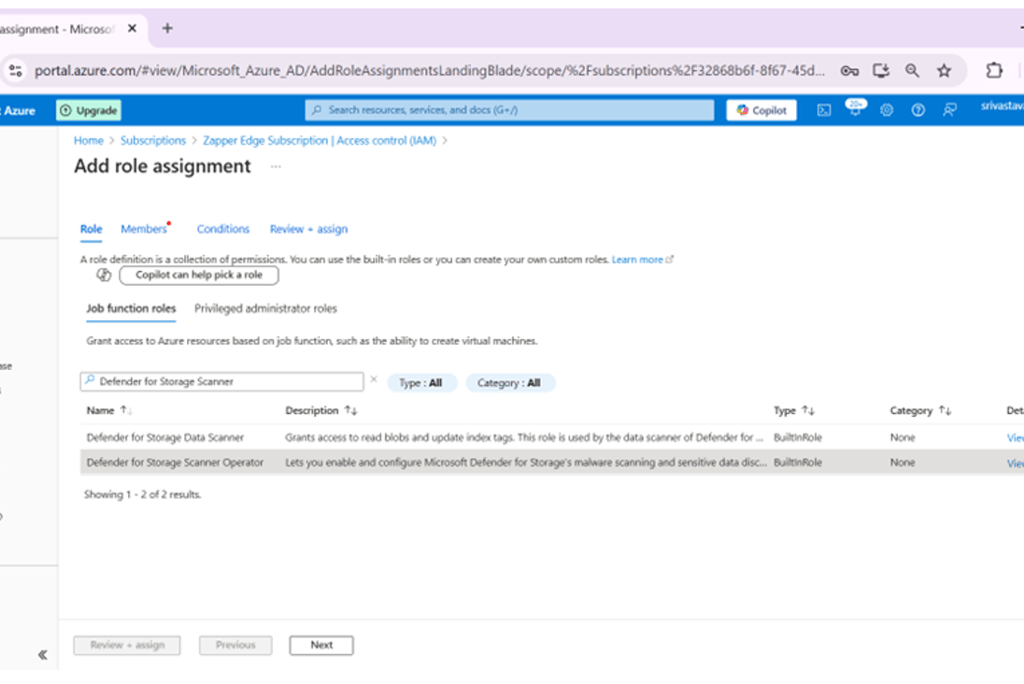
Searching for the Defender for Storage Scanner Operator role
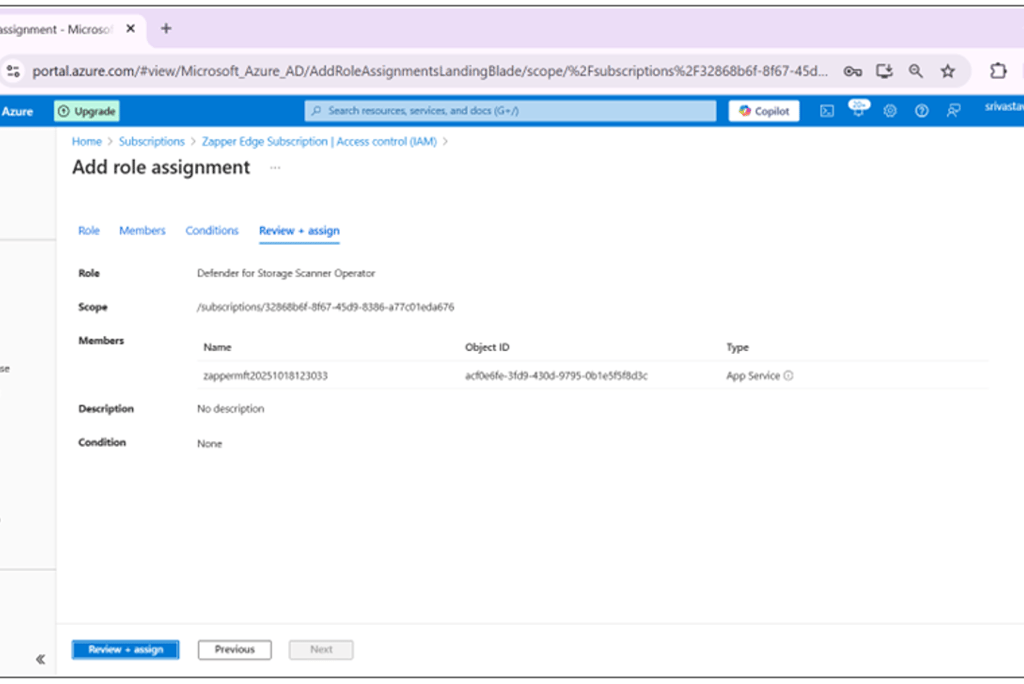
Reviewing and assigning the Defender for Storage Scanner Operator role
Refreshing Credentials
After granting the roles, wait a few minutes for the role assignments to propagate. Then restart your App Service or redeploy it to refresh its credentials. This forces the managed identity to obtain a new token with the updated permissions.
Validation Checklist
Before retrying to create a storage account, ensure that:
The Contributor role is assigned to the managed identity at the subscription level.
The Storage Blob Data Contributor role is assigned to the managed identity.
The Defender for Storage Scanner Operator role is assigned to the managed identity.
The App Service has been restarted or redeployed to refresh its credentials.
Need Help?
If the error persists after completing these steps, contact Zapper Edge Support at support@zapperedge.com.
Zapper Edge LLC
1621, Central Avenue,
Cheyenne, WY 82001, USA
Write to Us : Contactus@zapperedge.com



